 This is part two of my series on lesser known enhancements in the latest code for your VNX. Today we are going to focus on LDAP. You may remember my very popular post from last year on configuring LDAP for Unisphere. One of the big things I stressed before is that even with a Unified system, you still had to configure both the BLOCK & FILE side. Well, with the latest changes, that is a thing of the past. Now all the settings are done on the block side, and the new Unisphere Network Service will push them into the control station for you, simplifying the entire process.
This is part two of my series on lesser known enhancements in the latest code for your VNX. Today we are going to focus on LDAP. You may remember my very popular post from last year on configuring LDAP for Unisphere. One of the big things I stressed before is that even with a Unified system, you still had to configure both the BLOCK & FILE side. Well, with the latest changes, that is a thing of the past. Now all the settings are done on the block side, and the new Unisphere Network Service will push them into the control station for you, simplifying the entire process.
 Lets take a look at the configuration section. Just like it has been for the BLOCK side, you will find all the settings inside the “Domains” menu. You will notice right away that there is a new option to configure DNS. This is crucial for you to configure so that both the SPs and the control station can do host name lookups.
Lets take a look at the configuration section. Just like it has been for the BLOCK side, you will find all the settings inside the “Domains” menu. You will notice right away that there is a new option to configure DNS. This is crucial for you to configure so that both the SPs and the control station can do host name lookups.
- DNS Domain Suffix
- This is where you put in your domain suffix. This will be your primary domain namespace for lookups.
- DNS Server IP Address
- This is where you specify the IP addresses of your DNS servers. I recommend using at least 2 here.
- Domain Search List
- If you have multiple domains in your environment, this is where you would list them all in this area in order of search preference. Make sure your primary domain is at the top of the list.
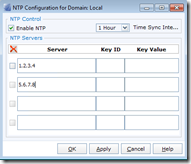
Just as important (in my opinion) as DNS, is configuring NTP. You can specify up to 4 NTP servers to keep your SP and Control Station times in sync. This really helps with comparing event logs against other sources. One thing to note, NTP server Keys support is unique to the SPs. It will not be copied over to the control station as it does not support it.
- Host Name or IP Address
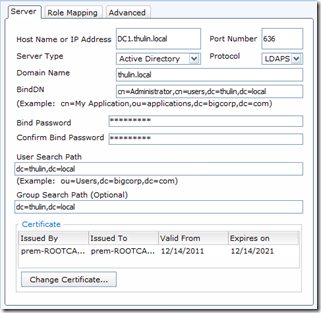
- This is where you put in the FQDN or IP of the domain controller. It is recommended to use the FQDN here, especially if you are using Secure LDAP.
- Port
- 389 for LDAP, 636 for LDAPS
- Server Type
- There are two options: LDAP Server and Active Directory. Make sure to choose “Active Directory” if you’re using an AD environment (most of you will be doing this)
- Protocol
- LDAP or LDAPS
- Domain Name
- Here you will specify the domain name being used
- BindDN
- This is where you put the distinguished name of the service account. For this example I just used the administrator account
- Bind Password
- Password for the service account
- Confirm Bind Password
- Make sure it matches
- User Search Path
- Just like with File, this is where you would set the search scope to find your users
- Group Search Path
- Just like with File, This is where you set the search scope to find your groups
- Add certificate
- This is where you would upload a root CA certificate for LDAPS. Make sure it’s in base64 encoding. You will need the entire certificate chain, so if you have multiple CAs in your chain, cut and paste them into the “cut and paste” section. The system will attempt to validate the certificate and let you know if there were problems during validation. Make sure you have DNS configured if you are going to do this.
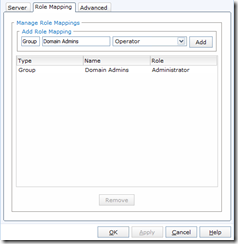 After you have put in all this information, click on the “Role Mapping” tab so we can map an AD group. In this updated version, individual LDAP user mapping has been removed, so make sure your AD groups contain only the users you want to give access. Put in the name of the AD group (in this example I used “Domain Admins”), then select the Role from the second pull down (in this case I selected Administrator), and finally click “Add” to add the mapping. Once you have all your mappings, click ok and wait for the confirmation message. The final addition is the ability to configure the level of nested group support in the advanced tab. By default, it is set to zero.
After you have put in all this information, click on the “Role Mapping” tab so we can map an AD group. In this updated version, individual LDAP user mapping has been removed, so make sure your AD groups contain only the users you want to give access. Put in the name of the AD group (in this example I used “Domain Admins”), then select the Role from the second pull down (in this case I selected Administrator), and finally click “Add” to add the mapping. Once you have all your mappings, click ok and wait for the confirmation message. The final addition is the ability to configure the level of nested group support in the advanced tab. By default, it is set to zero.
Once you have finished all this configuration, you will want to do this all over again for the second domain controller. Once you have this all set, click “Synchronize”. And that is it!
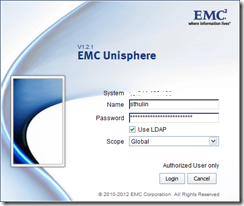
Now it is time to test your LDAP login. Logout of Unisphere by clicking the door icon in the upper right. Open Unisphere again and this time put in your AD username and password. Be sure to select “Use LDAP” and click on “Login”. If all your configuration is correct, you will be brought back in to Unisphere. If you get an access denied message, check you username, password, as well as your user and group search paths.
I hope you find this post useful. Let me know your own experiences with Unisphere LDAP Integration in the comments below.










 Twitter
Twitter LinkedIn
LinkedIn RSS
RSS Youtube
Youtube Picasa
Picasa Email
Email
